Communication, now more than ever, is the pulse of our modern society, and much of that credit goes to the telecommunications industry. It's the invisible force ensuring we stay connected, engage in commerce, and share information. But with great power comes challenges. DDoS attacks have emerged as significant threats, with their dynamics changing notably around the COVID-19 period. This article examines these attacks and their influence on Australia's telecommunications between 2020 and 2022. By analysing this period, we aim to understand the evolving landscape of DDoS threats and distil key lessons from these shifts.
The Pre-COVID-19 Era (2020)
The year 2020 witnessed a seismic shift in our digital interactions due to the global pandemic, leading to a surge in online activities. However, this surge in virtual presence also provided a breeding ground for cybercriminals to launch DDoS attacks, causing significant disruptions.
As COVID-19 forced people to work and learn from the confines of their homes, the reliance on the internet soared. Unfortunately, this dependence on digital platforms created opportunities for malicious actors to exploit vulnerabilities, resulting in disruptions across e-commerce, streaming services, online learning, and even healthcare.
Among the notable campaigns, the Lazarus Bear Armada campaign gained prominence for employing DDoS attacks to extort companies on a global scale. This campaign targeted industries crucial to everyday life, including e-commerce, streaming, online learning, and healthcare. These incidents highlighted the vital role telecommunications played in upholding a sense of normalcy.
To quantify the impact of DDoS attacks on the internet's infrastructure, the DDoS Attack Coefficient (DAC) emerged. This "DDoS tax" underscored the interconnected nature of the digital realm.
Throughout 2020, a diverse range of DDoS attacks unfolded, each varying in intensity and duration. These attacks utilised different methods, from DNS amplification to ICMP attacks. Notably, the Lazarus Bear Armada campaign distinguished itself by employing a spectrum of tactics.
DDoS Attack Statistics for 2020:
- Attack Frequency: Over 10 million DDoS attacks
- Maximum Throughput: 223 Gbps (Gigabits per second)
- Average Attack Duration: 10 minutes
- Attack Types: DNS Amplification, DNS, ICMP
- Maximum Number of Vectors in a Single Attack: 18 vectors
The numbers paint a picture of a world grappling with both pandemic and digital threats. Armed with this contextual understanding, we progress to explore the transformations that unfolded between 2020 and 2022.
The POST-COVID-19 Era (2022)
The passage of time ushered in changes by 2022. Companies fortified their defences, and attackers honed their tactics, reshaping the nature of DDoS attacks. This evolution sheds light on what we can call the "new normal" of DDoS attacks.
Even as the digital landscape continued to evolve, DDoS attacks persisted. NETSCOUT, equipped with advanced tools and expertise, diligently monitored and analysed threats, enhancing the preparedness of businesses against these adversities.
The methods of attack evolved in subtle ways. Notably, multivector attacks that combined different techniques emerged as indicators of attackers' sophistication. Among these techniques were Chargen Amplification and COAP Amplification.
Certain attack methods gained prominence, signalling shifts in attacker preferences. While familiar methods like TCP ACK and TCP SYN/ACK Amplification endured, new methods and changes in attack frequency came into focus.
DDoS Attack Statistics for 2022:
- Maximum Bandwidth: 803.26 Gbps (Gigabits per second)
- Maximum Throughput: 120.2 Mpps (Million packets per second)
- Average Attack Duration: 4 minutes
- Attack Frequency: 57,850 attacks
- TCP ACK: 46,112 attacks
- TCP SYN/ACK Amplification: 24,901 attacks
- TCP SYN: 21,696 attacks
- DNS Amplification: 21,118 attacks
- ICMP: 20,844 attacks
These shifts in tactics during 2022 imbued the statistics with fresh significance. Metrics such as maximum bandwidth, throughput, and attack duration unveiled a pattern of more intense yet briefer attacks. The increased frequency of attacks underscored the heightened attention cybercriminals were devoting to digital systems.
The Transformative Comparison: 2020 vs. 2022
A concise summary of attack statistics facilitates a clear grasp of the evolving DDoS landscape:
| Metric | 2020 | 2022 | Change |
| Max Bandwidth | 223 Gbps | 803.26 Gbps | +580.26 Gbps |
| Max Throughput | 21.2 Mpps | 120.2 Mpps | +99 Mpps |
| Average Duration | 10 minutes | 4 minutes | -6 minutes |
| Attack Frequency | Not specified | 57,850 attacks | |
| Attack Types | |||
| DNS Amplification | 54,325 attacks | 21,118 attacks | -33,207 |
| CLDAP Amplification | 42,900 attacks | Not specified | |
| ICMP | 41,529 attacks | 20,844 attacks | -20,685 |
| TCP ACK | 17,678 attacks | 46,112 attacks | +28,434 |
| TCP SYN | 11,717 attacks | 21,696 attacks | +9,979 |
This comparative analysis reveals a world navigating a pandemic and digital threats in tandem. With this backdrop, we proceed to examine the transformation between 2020 and 2022.
The evolution of the DDoS landscape in 2022 becomes evident. The challenges faced by the telecommunications industry shifted, demanding swift responses to evolving threats. Amidst these changes, the sector's resilience remains steadfast as it stands up against digital perils.
Industry Focus: A Closer Look
Ranking of Most Targeted Sectors: 2020 vs. 2022
| Rank | Industry | 2020 Frequency | 2022 Frequency |
| 1 | Wired Telecommunications Carriers | High | High |
| 2 | Wireless Telecommunications Carriers | High | Moderate |
| 3 | Data Processing, Hosting + Related Svc | Moderate | Low |
| 4 | Electronic Computer Manufacturing | Moderate | Low |
| 5 | Electronic Shopping + Mail-Order Hse | Moderate | Low |
| 6 | Software Publishers | Low | Low |
| 7 | Internet Publishing, Broadcasting | Low | Low |
| + Web Search Portals | |||
| 8 | Other Telecommunications | Low | Low |
| 9 | Landscaping Services | Low | Very Low |
| 10 | Other Services Related to Advertising | Low | Very Low |
Lessons Learned: Adapting to a Shifting Landscape
Comparing the most targeted sectors between 2020 and 2022 highlights a discernible shift in focus and intensity within DDoS targeting. Industries heavily targeted in 2020 experienced varied changes in attack frequency by 2022, reflecting the evolving strategies of cybercriminals and shifts in industry priorities.
Consistent Targeting: Telecommunications
Wired and wireless telecommunications carriers remained consistently high on the list of the most targeted sectors. This underscores the ongoing relevance of attacking vital communication infrastructure.
Shifting Landscape: Data Processing and Hosting
The sector encompassing data processing, hosting, and related services displayed a noteworthy transition from moderate targeting in 2020 to becoming a lower-priority target in 2022. This could indicate a shift in cybercriminal focus towards other sectors or a response to improved defences within this industry.

Stability in Wireless Telecommunications
Wireless telecommunications carriers, moderately targeted in both years, exhibited a consistent targeting trend. This suggests that the sector's centrality in mobile communications maintained its attractiveness to attackers.
Diverse Targeting
Sectors like electronic computer manufacturing, electronic shopping, and mail-order houses, along with software publishers, experienced varying degrees of targeting. This diversity implies that cybercriminals are diversifying their efforts to exploit vulnerabilities across different industries.
Steady or Decreasing Targeting
Industries such as internet publishing, broadcasting, web search portals, and those related to physical distribution and logistics consulting services remained relatively stable in targeting frequency or witnessed a reduction in attacks.
Industry Response: Preparedness and Resilience
The shifts in attack targeting underscore the diverse responses of different industries to the evolving threat landscape. Some sectors might have fortified their cybersecurity measures, making them less enticing targets, while others could have become more susceptible due to operational changes.
Evolving Together: DDoS Evolution and Lessons Learned
The evolution of DDoS attacks exemplifies a valuable lesson in resilience, adaptability, and progress at the crossroads of technology and communication. As these DDoS attack scenarios evolve, fortifying defences and assessing the resilience of digital assets against potential threats becomes increasingly imperative for organisations. Whether safeguarding nodes, endpoints, web servers, cloud infrastructure, applications, networks, or the overarching topology, preparing for DDoS attacks emerges as a paramount priority.
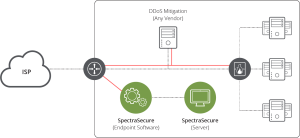
One effective solution in this domain is NETSCOUT’s SpectraSecure DDoS resiliency test tool. This DDoS Stress Testing solution empowers organisations to assess and enhance their readiness against DDoS attacks. By subjecting various components of their digital infrastructure to simulated attack scenarios, organisations can identify vulnerabilities, optimise response strategies, and ensure continuity in the face of disruptions.
In a realm characterised by innovation and security, Australian telecommunications play a pivotal role - connecting, remaining resilient, and maintaining unwavering vigilance. As we conclude this chapter, let us remember that these lessons propel us toward a promising digital future, secure and interconnected.